Everything in the modern era is connected! This is the world of the internet and the web. The world that makes our lives easier, but at the same time, crosses the boundaries of “privacy” and can sometimes be a hostile place. Everything is connected via “The Web,” and the Web uses servers as a source of information storage. These servers are an asset to everyone who owns them. A web server delivers information such as web pages, images, videos, and other data types available to the client when requested.
As the importance of a server suggests, a web server runs on the back-end of an application constantly and should not be halted at any point in time. Doing so can have serious impacts on the organization of the application. A web server is of prime importance within the internet infrastructure. The Apache HTTP Server is the most widely used web server these days.?
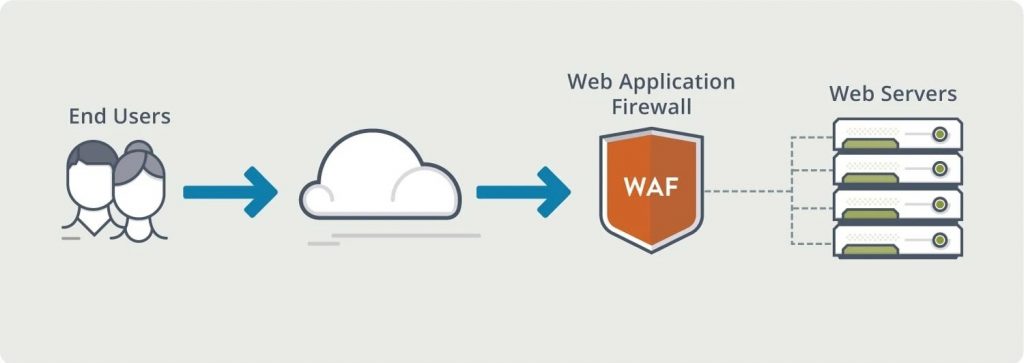
Introduction to Web Application Firewalls (WAFs)
These web servers need “firewalls” to protect from malicious hosts and web server attacks. These firewalls are commonly referred to as Web Application Firewalls (WAFs). A WAF is mainly divided into two categories:
“Open Source,” meaning it is free to use and can be accessed by anyone in the world for free.
The second category is “Closed Source,” which, as the name suggests, is a proprietary WAF and can be accessed only by certain people (usually the organization that makes it). It is not easily available and is also not free to use.
Open-Source WAF
An open-source WAF is a software designed to detect, protect, and secure web servers amidst hostile web attacks from malware. It can prevent attacks capturing a web server’s vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), File Inclusion and Improper Configuration, etc. Injection attacks refer to injections perpetuated through SQL, OS, and LDAP. Malicious data is sent to the website and executed by the program through these attacks. Cross-Site Scripting, also known as XSS, happens when volatile and suspicious data goes through invalidated parameters. File inclusion refers to the point where improper and unauthorized files are included.
Open source WAF is the first line of defense for a web server and a web application. It works similarly to a proxy site. As a proxy site works to hide the credentials of its client, an open-source WAF works similarly as an intermediary that protects the web applications and servers from attacks. An open-source WAF is typically user, session, and application-aware, conscious of the web apps behind it and what services they offer. You can think of a WAF as the intermediary between the user and the app itself, analyzing all communications before reaching the app or the user. Traditional open source WAFs ensure only allowed actions (meeting the security policy) can be performed.
The SANS Institute describes the working principle behind an open-source WAF. They use a mixture of rule-based logic, parsing, and signatures to detect the threats that may occur to the web application and the web servers.
Open Web Application Security Project
The OWASP (Open Web Application Security Project), the society that provides the methodologies, rules, and tools for the web application, provides the ten minimum security flaws that each open source WAF has to follow as mentioned:
- Injection
- XML External Entities (XXE)
- Sensitive Data Exposure
- Broken Authentication
- Broken Access Control
- Insufficient logging and monitoring
- Security Misconfigurations
- Cross-Site Scripting (XSS)
- Insecure Deserialization
- Using components with known vulnerabilities
Three Different Methods to Deploy
All the commercial open source WAFs cover these ten security flaws minimum. An open-source WAF is also somewhat different from regular firewalls. While other firewalls protect the user and applications from outside threats, an open-source WAF prevents the web server from malicious attacks. This type of firewall is considered a “reverse proxy” where instead of detecting and preventing threats for the user, the proxy detects and prevents traffic for the webserver. Another difference between an open-source WAF and other firewalls is how they are deployed; instead of being where the user is, an open-source WAF is deployed from the front, typically where the application is.
An open-source WAF is commonly deployed in three different methods according to NSS Lab’s open source WAFs are deploying options are:
- Transparent Bridge
- Transparent Reverse Proxy
- Reverse Proxy
The term “transparent” means that web traffic is sent to the open-source WAF first and then to the server. An open-source WAF can be deployed anywhere with relative ease, and it mostly depends on where the application is launched and mainly the types of services required for the application.
Advanced Modes for The Deployment
The deployment can often vary considering the architectural flexibility and the way of managing and application. The management model and available resources are big credentials in deploying an open-source WAF. Following are some advanced modes for the deployment of an open-source WAF:
- Cloud-Based and managed as a service
- Cloud-Based and Self-managed
- On-premise Advanced WAF
- Cloud-Based and Auto provisioned
Most Popular Open Sources WAFs
Thousands of web applications and websites get hacked each day due to volatile code and malicious threats following are some of the most popular open sources WAFs used commonly nowadays:
- ModSecurity by TrustWave is one of the most widely used open-source WAF; it supports Apache HTTP, Microsoft IIS, and Nginx.
- NAXSI is the only open-source WAF created for protection against SQL Injection and Cross-Site Scripting.
- WebKnight is the open-source WAF for Microsoft IIS.
- ShadowDaemon is another open-source WAF that comes with its dynamic interface and supports PHP, Perl, and Python frameworks.
Final Verdict
An open-source WAF is a paramount tool used for securing web servers and applications and can be easily deployed. They are open-source; hence anyone can use them for free. Furthermore, open-source WAFs protect against malicious malware and threats to web applications and servers. Key features include easy deployment, detection, protection, and prevention from threats and security for server-side applications.
They are being widely used in modern websites and web applications for security and are quite widespread these days. The modern era advancements require open-source WAFs for better security and protection.

As the editor of the blog, She curate insightful content that sparks curiosity and fosters learning. With a passion for storytelling and a keen eye for detail, she strive to bring diverse perspectives and engaging narratives to readers, ensuring every piece informs, inspires, and enriches.









